Original source: Odaily Planet Daily
Original author: Nan Zhi
Munchables suffers insider attack
At 5 a.m. today, the Blast ecological project Munchables posted a message on the X platform stating that it was under attack. According to Paidun, there was a suspected problem with the Munchables locking contract, resulting in the theft of 17,400 ETH (worth approximately $62.3 million).
Munchables is one of the Blast BIG BANG competition champion projects. It is a chain game project based on NFT pledge. In the early stages of the development of the protocol, users can mint NFT for free by pledging 1 ETH or equivalent tokens, locking the NFT for 30 days, and there are additional incentives to encourage users to lock for longer. Pledged assets can obtain a series of rights and interests such as Blast points + gold points + protocol governance tokens. For example, NFT whale dingaling once announced that it pledged 150 ETH in the protocol.
At present, the project has completed a Pre-Seed round of financing, with Manifold and Mechanism Capital co-leading the investment. The financing amount has not yet been disclosed.
North Korean hackers appear again
After the attack last night, on-chain security detective ZachXBT was the first to point out that the attack was related to a North Korean developer and released his resume.
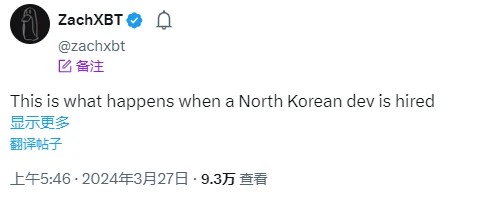
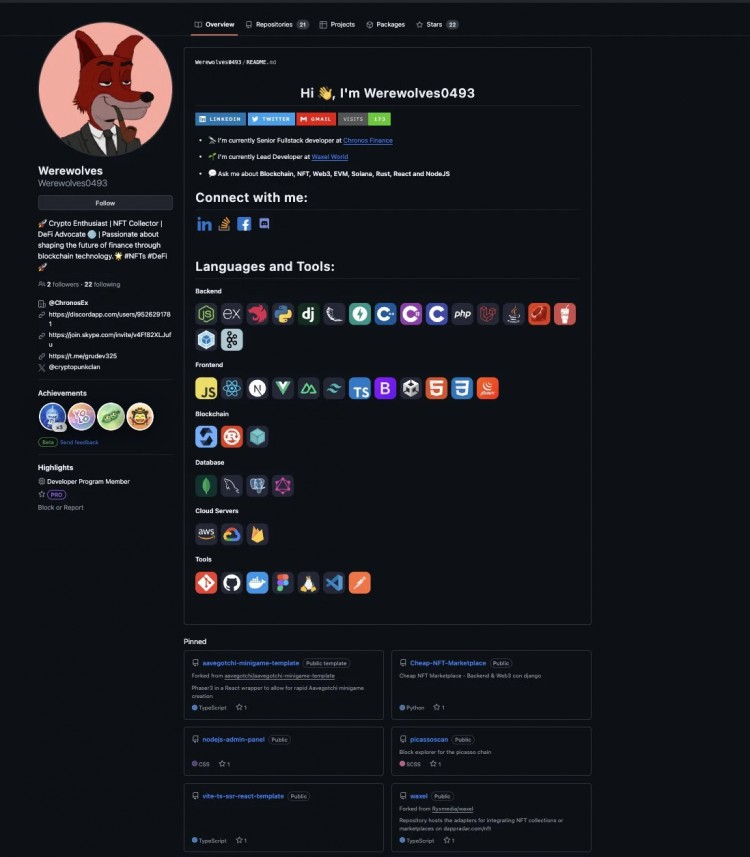
This morning, Slow Mist Cosine posted on the The perpetrator is a North Korean hacker... This is at least the second time we have encountered such a situation with a DeFi project. The core developer has been lurking in disguise for a long time, gained the trust of the entire team, and struck when the time comes..."
Afterwards, CoderDan, the founder of Aavegotchi, posted on the Fired him within a month. He also tried to get us to hire a friend of his, who was probably also a hacker." CoderDan added that Pixelcraft Studios had some video calls with him at the time, but they were not recorded. It's unclear whether Google records all video calls internally, but the hacker did show up.
Finally, CoderDan provided the Munchables team with the hacker’s usual address when he worked at Pixelcraft Studios, hoping to use these clues to help Munchables recover the funds.
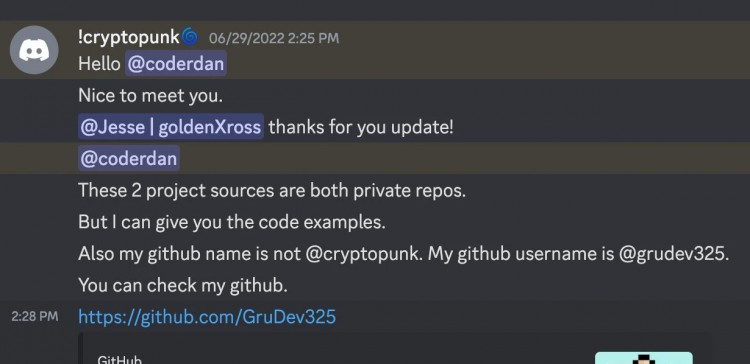
As of now, there is no particularly direct evidence to prove the true identity of the hacker, but multiple testimonies have revealed the North Korean hacker behind this incident.
Why do security incidents occur?
According to on-chain analyst @SomaXBT, the Blast ecosystem stolen project Munchables previously hired an unknown security team, EntersoftTeam, to issue an audit report in order to save audit fees. The team’s account profile reads “We are an award-winning application security company with certified white hat hackers,” but the platform only has a few hundred followers.
The latest news, according to ZachXBT analysis, is that the four different developers hired by the Munchables team may all be the same person. They recommended each other to do the job and made regular transfers to the same two exchange deposit addresses, as well as each other's wallets. top up.
The attacker has a sudden conscience?
At 14:00 p.m., according to monitoring by the on-chain data analysis platform Scopescan, the Munchables attacker returned all 17,000 ETH to a multi-signature wallet 0x 4 D 2 F. At that time, it was not sure whether it was a refund or a transfer address for the attacker.
Half an hour later, Blast founder Pacman announced on the Currently worth $96 million). Kudos to the former Munchables developer for choosing to finally return all funds without any ransom. Munchables also forwarded this announcement saying: "All user funds are safe, no locks will be enforced, and all Blast-related rewards will be distributed. Updates will be made in the coming days."
At the same time, Juice, which was previously affected by the Munchables attack, also announced the safety of its funds. All its wETH has been retrieved from the Munchables developers. Juice is coordinating with Pacman and Blast to transfer wETH back to Juice so that users can withdraw funds.
We don’t know the story behind why the attacker suddenly found out about the refund. Last night, he conducted a cross-chain coin laundering through the third-party cross-chain bridge Orbiter, but the amount was only 3 ETH. It takes 14 days to transfer through the official cross-chain bridge, and the third-party cross-chain bridge has insufficient liquidity, which may ultimately make it difficult to effectively transfer funds, leading to its negotiation for refunds.
in conclusion
In the past, when new chains were initially launched, due to mixed teams and incomplete infrastructure, it was not uncommon for projects to run away with money or be attacked by hackers. In the early days, there were also incidents of lack of supervision and theft of members by early teams. We cannot count on it every time. The attacker transformed into a white hat "conscience discovery" and refunded money, recommending investors to DYOR and strictly control the allocation of investment positions.
