背景
2024年1月16日,有部落客在中國社群平台爆料緬甸聯軍涉嫌向滯留在緬甸的電子詐騙產業從業者強行收取高額加密貨幣,並展示了他們聲稱使用的加密貨幣地址收取款項。 目前,該爆料已在網路上廣為傳播。
本文由 Bitrace 與 MistTrack 共同針對已揭露地址的加密資金進行分析,包括:地址資金收付規則、地址資金來源風險、關聯地址活動等,旨在揭露相關分析內容。
地址行為分析
(https://mp.weixin.qq.com/s/WDWM22vw68-NsVr0_1jHfA)
上圖為爆料文章中的資訊。 基於此,研究人員對公開的支付地址TKFsCN進行了USDT匯率分析,並試圖透過某些特定金額的USDT收據來推斷其背後的結算單位。
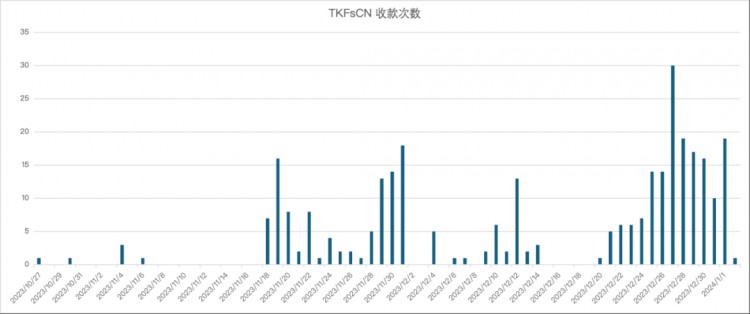
該支付地址的歷史交易記錄顯示,該地址收到的USDT單筆交易包含大量不完整的十、百個數字,如71417、42857等數字。 當交易以非美元結算時,這種情況很常見。 研究人員嘗試計算主要法幣兌USDT的匯率後發現,這些交易疑似以1美元:7-7.2人民幣的匯率進行結算,單筆資金轉帳金額在50萬元人民幣不等。至 600,000。 在100萬、150萬的幾個區間存在著聚集現象。
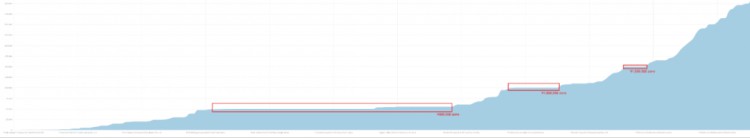
過濾掉100 USDT及以下交易金額後,統計顯示,TKFsCN共307筆USDT轉帳金額中,有193筆是基於人民幣兌美元匯率進行的轉帳。 交易筆數佔總數的62.86%,交易金額佔總數的62.86%。 佔總數的45.29%。
這表示該地址收集的交易中超過一半以人民幣結算,且以50萬兌換金額的轉帳為主。 支付USDT的一方必須是中國人。
資金來源分析
原文提到,「佔領老街後,中國人(筆者註:電子詐騙產業從業人員)到處被捕,如果願意付費自保,付費的可以送走,不付費的可以送走。」不付款就會被送到中國。” 如果屬實,TKFsCN的交易應該存在大量新的交易對手,並且部分資金來自灰黑資產、洗錢、詐欺等相關地址。
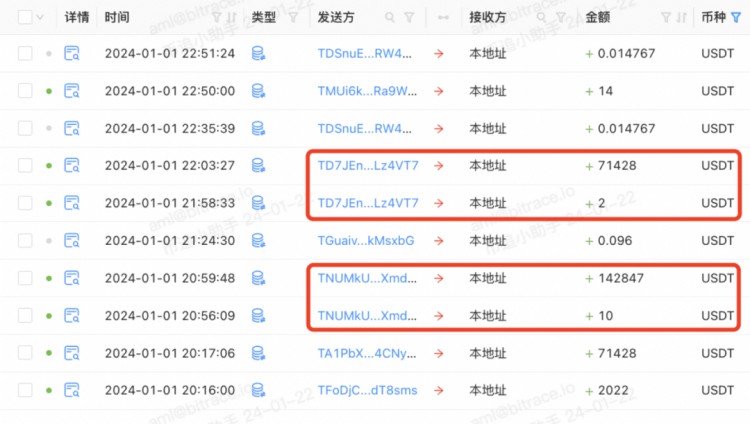
The data shows that between October 22, 2023 and January 2, 2024, TKFsCN received a total of USDT transfers from 182 direct counterparties, of which 117 addresses had two consecutive transfers of small amount + large amount. feature. This is a typical transfer test behavior. The payer does not choose to complete the transfer in one go in order to confirm that the address is correct. This shows that at least 62.29% of the counterparties may be making transfers for the first time and are not regular trading partners of TKFsCN.
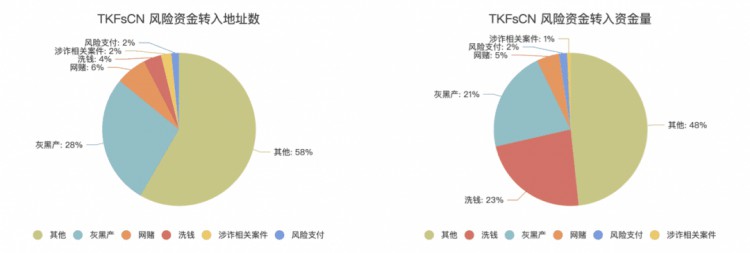
A more in-depth audit of the address risk funds of TKFsCN showed that the counterparty transferring funds to this address is closely related to black and gray industry, online gambling, fraud, money laundering, risk payment and other activities. Among the 182 direct transfer parties, up to 42% were addresses associated with risk activities, transferring USDT worth $33,523,148 to TKFsCN.
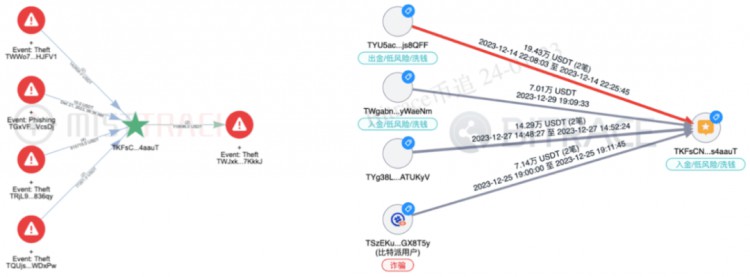 (Images from MistTrack and BitracePro)
(Images from MistTrack and BitracePro)
It is worth noting that among this batch of addresses associated with risky activities, investigators also found 7 addresses that were clearly related to known criminal cases, including two money laundering cases, one fraud case, one online gambling case, and one telephone fraud case. , and the suspects are all located in northern Myanmar or Cambodia.
This shows that the counterparty address that initiated payments to TKFsCN is not only involved in a large number of risky crypto activities, but is also closely related to criminals in Southeast Asia.
Another strange thing is that investigators also found a money laundering address related to a telecom fraud case in the transfer address, indicating that there are also certain doubts in the traceability analysis of some of the fund flows from the transfer address. This doubtful point will be non-sensitively expanded in the "Related Address Analysis" section below.
Based on the cluster analysis of the above-mentioned TKFsCN address, it was found that this address is suspected to have a subject clustering relationship with nearly a hundred addresses. Some of the addresses not only have similar fund collection and payment activities to TKFsCN, but also reveal more information about the payee. , taking the payee TKKj8G as an example:
TKKj8G directly received 6 funds from TKFsCN totaling more than 4.6 million USDT, and is one of the collection addresses in the payee’s subsequent fund link;
TKKj8G is one of the core payment addresses. Among the 60 payments with an amount exceeding 100 USDT, up to 50 payments have small-amount testing behavior similar to TKFsCN;
TKKj8G became active on August 18, 2023, much earlier than other addresses, and had transactions with Huiwang Guarantee during this period - receiving 160,000 USDT from the Huiwang Guarantee address, which was analyzed as a merchant guaranteed by Huiwang Guarantee Get the deposit back from Huiwang Guarantee.
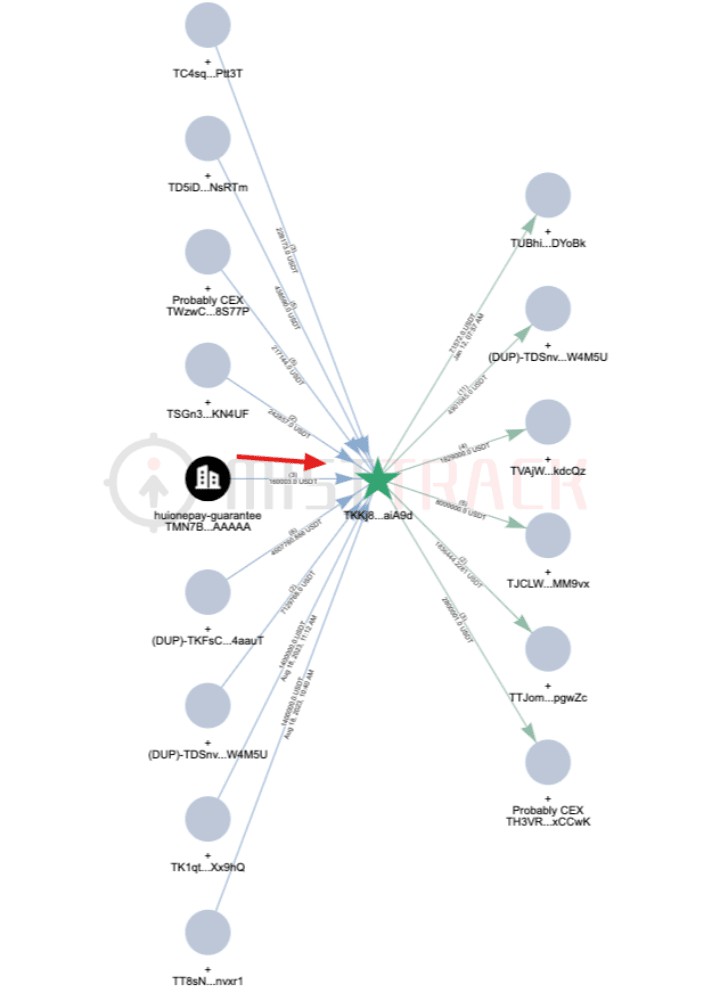
This indicates that the "Ministry of Finance Address" mentioned in the original article may not exist. The address set including TKFsCN and TKKj8G should belong to a digital currency acceptor located in northern Myanmar or Cambodia, and for some reason collects these payments on its behalf. .
To sum up, it is not difficult for investigators to outline a typical payer portrait - engaged in illegal work in Southeast Asia, and for some reason had to pay USDT worth 500,000 yuan to a collection address. Since this was the first transaction, a small test was conducted before transferring a large amount to prevent address errors. The cryptocurrency used for payment either comes from its original illegal gains or is purchased from other illegal entities.
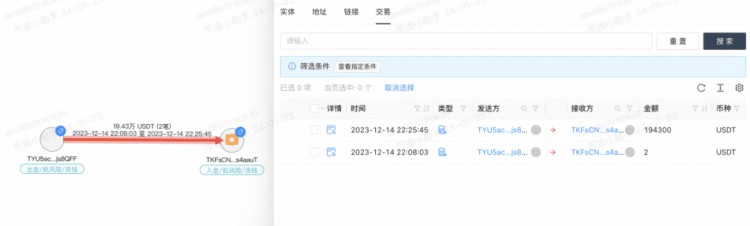
But this is not the case for all payers. Investigators also found some addresses that did not meet or did not fully meet such characteristics. Take TYU5acSGRwsYJfBhdpQc3broSpfsjs8QFF as an example. This address is one of the 7 addresses directly involved in the case mentioned above, and the other 6 The address transferred cryptocurrency worth RMB 500,000, RMB 500,000, RMB 1 million, RMB 1 million, RMB 2.7 million (1.50 + 1.2 million), and RMB 550,000 to TKFsCN respectively, but the transfer amount of TYU5ac was converted to RMB 1.36 million at the same exchange rate. Although it is an integer, this particular amount is still very different from other addresses.
Investigators have no way of knowing why. Considering the small-amount testing behavior at this address, a reasonable guess is that the transactions behind this address represent three combined transfers worth 500,000 yuan, and obtained a 10% discount.
This article conducts an in-depth analysis of the rules of fund collection and payment from public addresses, address fund source risks, and associated address activities, and discloses relevant analysis content. The main conclusions are as follows:
1. More than half of the transactions collected by the target address of this analysis are settled in RMB, and transfers with conversion amounts of 50, 1 million, and 1.5 million dominate;
2. The counterparty address that transfers funds to the analysis target address is closely related to black and gray industry, online gambling, fraud, money laundering, risk payment and other activities;
3. The target address and its associated addresses already had traces of risky business activities before intensive collection of such funds. After cluster analysis of the analyzed address, it was found that the cluster was suspected to be a merchant guaranteed by Huiwang;
4. The counterparty address that initiated payment to the analysis target address is closely related to criminals in northern Myanmar or Cambodia.
綜上所述,《盟軍虛擬貨幣帳戶曝光,向北方人勒索數億虛擬貨幣》一文中揭露的部分資訊與鏈上事實相符。 確實有大量的中國電子詐騙產業位於緬甸北部或柬埔寨。 從業者集體將人民幣整數金額的USDT資產轉移到某組地址,但這組地址可能不是所謂的“財政部地址”,而是當地數位貨幣受理機構的地址,這與原來的文章。
關於我們
這項調查是由 MistTrack 和 Bitrace 的調查人員進行的。
MistTrack(https://misttrack.io/) 是由區塊鏈安全公司慢霧(SlowMist)開發的反洗錢追蹤系統,專注於打擊加密貨幣洗錢活動,對所有者開放使用。MistTrack 反洗錢追蹤系統積累有了2億多個地址標籤,能夠識別全球主流交易平台的各類錢包地址,包含1千多個地址實體、超40個威脅情報資料和超9千萬個風險地址。
Bitrace(https://www.bitrace.io/)是一家區塊鏈資料分析公司,為Web3企業、金融機構和監管及執法部門提供領先的加密貨幣資料分析、風險管理、執法協作等合規、監管工具產品與服務支援。
免責聲明
本文內容基於反洗錢追蹤系統 MistTrack 以及加密貨幣追蹤與分析平台 BitracePro 的數據支持,旨在對網路上公開的地址進行分析文件分析結果進行披露,但由於區塊鏈的特性,我們在此並不能保證所有數據的絕對準確性,也不能對其中的錯誤、疏漏或使用本文內容造成的損失承擔責任。同時,本文不構成任何立場或其他分析的依據。
